0%

KATHMANDU: In 2021 and throughout 2022, the Federal Bureau of Investigation (FBI), the federal law enforcement and intelligence agency of the United States, received a significant number of complaints from American victims, with a substantial portion being elderly, retired, or in ill health.
These victims fell prey to a widespread fraud scheme in which their funds were covertly transferred to multiple accounts. The FBI initiated a comprehensive investigation spanning multiple countries, including the United States, India, Canada, and Nepal.
During this investigation, the FBI meticulously gathered statements from hundreds of victims and accumulated substantial evidence.
This evidence revealed a significant revelation that the stolen funds of the victims were being funneled to Nepal through diverse channels, including direct financial transactions associated with Prithvi Bahadur Shah, a crucial figure in the Nepalese aspect of the investigation, and over a dozen of his company bank accounts of a large-scale wire fraud scheme targeting vulnerable U.S. citizens, private enterprises and foundations.
In collaboration with Canadian and Indian law enforcement agencies, the FBI successfully identified members of the Fraud Ring and their financial connections in Nepal.
As the FBI investigation unfolded across multiple countries including the United States, India, Canada, and Nepal, it was discovered that a significant number of U.S. victims had their personal funds transferred to Nepali bank accounts.
Evidence suggested that victims’ personal computers were accessed by the Fraud Ring under the pretext of legitimacy such as working on behalf of legitimate technology companies and antivirus companies and stealing money from U.S. citizens’ bank accounts, and unwittingly transferring money into bank accounts controlled by Prithvi Bahadur Shah in Nepal.
The technical assessment proved that Shah had direct links to the fraudulent ring in the United States, Canada and India.
This transnational organized criminal network had cleverly established numerous bank accounts using different aliases to disguise their illicit transactions, making them appear legitimate and genuine.
The FBI successfully identified the fraudulent companies and other associated activities as “Fraud Entities.”
These entities lacked any legitimate economic function or operational business activities.
The fraudulent scheme specifically targeted vulnerable U.S. citizens, including people with Alzheimer’s disease, cancer, elderly, as well as private enterprises, and charitable organizations.
Despite receiving widespread criticism from various sectors of society, including political figures, economists, and former central bank governors, who urged the government not to take such action, their appeals were unfortunately disregarded.
Through stealthy means, a staggering amount of over $4 million was transferred to Nepal as part of this fraudulent operation.
Within the United States, the FBI carried out thorough and comprehensive investigations into the criminal gangs involved in the fraudulent scheme.
These investigations encompassed a detailed examination of their previous activities, the potential methods they employed for their illicit transactions, and their communication networks on a global scale.
Investigators made a significant discovery during their probe, uncovering that the criminals employed remote desktop applications as a means to defraud individuals.
These applications were utilized under the guise of providing technical support, allowing the perpetrators to carry out their fraudulent activities.
Additionally, the gangs cleverly leveraged Voice over Internet Protocol (VoIP) technology for their phone calls, enabling them to make calls over the Internet and evade detection.
The Fraud Ring employed a deceptive tactic to manipulate victims into believing that their personal computers were infected with viruses or malware.
Exploiting this fear, they would then convince the victims to transfer hundreds or even thousands of dollars into designated accounts.
This manipulation allowed the Fraud Ring to exploit the victims’ trust and exploit their financial resources for illicit gain.
While the investigation into the criminal fraud ring was underway, it became evident that the primary targets of their malicious activities were vulnerable U.S. citizens, particularly elderly and retired individuals.

The fraud ring employed various schemes, such as computer virus update scams and technical support fraud, to exploit their victims.
Despite the ongoing investigation, the fraud ring continued to exploit the trust and vulnerability of these individuals for their illicit gains.
A portion of the stolen money was discovered to have been funneled into Nepali banks under multiple company names.
These illicit transactions allowed the perpetrators to conceal the origin of the funds and further complicate the investigative process.
As the investigation into the transnational gangs linked to Prithvi Bahadur Shah’s international wire fraud unfolds, it came to light that these criminal entities have been engaging in covert and illicit transactions to siphon off money from their victims through various means.
The Nepal Rastra Bank then sent a letter to the Central Investigation Bureau (CIB) of the Nepal Police and the Department of Money Laundering Investigation, urging them to investigate Shah and his associates.
To facilitate their fraudulent activities, gang members resorted to fabricating paperwork and establishing sham companies. This included forging U.S. passports, and driver’s licenses of U.S. citizens, and utilizing stolen documents, such as social security numbers, to facilitate money transfers.
Furthermore, these criminals employed deceptive tactics involving fraudulent Memorandums of Understanding (MoUs) and other fabricated paperwork to access and withdraw funds from Shah’s companies’ Nepali bank accounts.
This sophisticated network of illegal activities further complicated the investigation into their illicit operations.
As the FBI investigation unfolded across multiple countries including the United States, India, Canada, and Nepal, it was discovered that a significant number of U.S. victims had their personal funds transferred to Nepali bank accounts.
In light of the concerning circumstances, the U.S. Financial Crimes Enforcement Network (FinCEN) took swift action by urgently requesting Nepal’s Central Bank’s Financial Information Unit (FIU) to intervene.
To aid in the investigation, FinCEN provided the FIU with a list of suspicious bank accounts in Nepal.
The intention behind this request was to implore the Nepalese authorities to promptly freeze these identified accounts to prevent any further transactions from taking place.
This collaborative effort sought to disrupt the illicit activities of the criminal network and safeguard the funds of the victims involved.
Following FinCEN’s request, Nepali banks promptly responded by placing holds on several accounts associated with Shah’s companies and their affiliates.
The cumulative amount held in these frozen accounts amounts to USD 1,560,577.
While specific details of the frozen accounts are not available, it was encouraging to see immediate action being taken to safeguard the stolen money of U.S. victims.

During that period, several U.S. victims personally emailed the related banks, including Kumari Bank, requesting them to halt the transactions of their money stolen by gang members in the name of tech support.
Following the urgent request from FinCEN, the Central Bank of Nepal (Nepal Rastra Bank) instructed private banks to freeze suspicious accounts.
In Nepal’s government headquarters at Singha Durbar, Finance Minister Janardan Sharma (at that time) exerted pressure on the Nepal Rastra Bank to release funds that had come from foreign investment to Nepal.
Under Minister Sharma’s direction, the then Finance Secretary Madhu Kumar Marasini issued a written request to the central bank, demanding the unconditional release of the funds, to which the central bank refused to comply.
The Nepal Rastra Bank then sent a letter to the Central Investigation Bureau (CIB) of the Nepal Police and the Department of Money Laundering Investigation, urging them to investigate Shah and his associates.
Despite ongoing investigations in the United States, Canada, and India, Nepal’s Department of Money Laundering decided to unfreeze Shah’s bank accounts due to potential political influence from Janardan Sharma and some of close associates of the Prime Minister Sher Bahadur Deuba (at that time).
Retired Deputy Inspector General (DIG) Hemanta Malla Thakuri, a highly-respected police investigator in Nepal, who has gained recognition for his successful resolution of numerous high-profile criminal cases during his tenure as the Executive Director of the Central Investigation Bureau (CIB), shared his views on the Prithvi Bahadur Shah wire fraud case.
He expressed concerns about the implications of the case on the nation’s integrity and international standing.
“When Nepal is expected to conduct an inquiry into such cases initiated by the United States, the provision of protection to the accused by those in power, including Cabinet ministers, raises serious doubts about the credibility of the nation and its government,” he stated.

Malla emphasized the importance of cooperation between the United States and Nepal in investigating wire fraud cases.
He further emphasized that such actions create a crisis of confidence and trust deficit on the international stage, thereby undermining the integrity of the country.
Meanwhile, on January 25, 2022, the Department of Money Laundering under the Prime Minister’s office gave Shah a clean cheat.
On January 31, 2022, the Department of Money Laundering issued a letter to the Nepal Rastra Bank, requesting assistance in the process of unfreezing multiple accounts belonging to Shah.
The Department argued that the currently available evidence did not establish Shah’s involvement in money laundering or suspicious transaction from abroad.
Amid the crisis between the then Finance Minister Sharma and the Nepal Rastra Bank regarding the freezing of funds, on April 8, 2022, Finance Minister Sharma proposed to the Cabinet the “sacking” of Governor Maha Prasad Adhikari.
This decision was made due to Adhikari’s refusal to unfreeze Shah’s funds despite explicit instructions from minister Sharma and other high-ranking cabinet officials.
In response, the Cabinet formed a three-member probe committee led by former Supreme Court justice Purushottam Bhandari to carry out an investigation on the central bank Governor. It is worth noting that Bhandari is a relative of the Finance Minister Sharma (at that time). As a consequence, Governor Adhikari was suspended.
During a period when Nepal’s economy and foreign reserves were already facing significant challenges, the government chose to suspend the Governor due to personal reasons related to Sharma’s intention to release Shah’s funds.
They deceitfully obtained more than $4.54 million, £22,000 sterling, and CAD 340,000 (equivalent to NPR 639.5 million) by stealthy money of foreign nationals under the guise of investment in Nepal. It is important to note that these funds were obtained through wire fraud schemes primarily targeting elderly American citizens.

Despite receiving widespread criticism from various sectors of society, including political figures, economists, and former central bank governors, who urged the government not to take such action, their appeals were unfortunately disregarded.
Governor Adhikari filed a writ petition in the Supreme Court, seeking an interim order to reinstate his position.
Despite his suspension by the cabinet, Prime Minister Sher Bahadur Deuba (at that time) and Chairman of the coalition partner Maoist Centre, Pushpa Kamal Dahal (now Prime Minister), personally contacted various individuals to exert influence on the potential verdict of the Supreme Court.
This included reaching out to a former Chief Justice, requesting his support for the government’s decision to remove the Governor.
However, the former Chief Justice refused to cooperate and instead advised them to address the root cause of the economic turmoil and mismanagement by removing the then Finance Minister Sharma.
The conversation ended abruptly with the Chief Justice hanging up the phone.
The Supreme Court issued an order to the government, instructing them not to implement the cabinet decision to suspend the Governor.
Additionally, the court revoked the inquiry committee due to the conflict of interests involving finance minister Sharma. Following the court’s verdict, Governor Adhikari returned to the Central Bank and resumed his duties.
During Prime Minister Deuba’s tenure and with Sharma as the Finance Minister, no investigation was conducted regarding the Shah case.
The U.S. government had long requested an investigation into Shah’s activities, but due to the vested interests of influential politicians, the investigation remained pending until a new government was formed.
Numerous online complaints and email requests were filed by U.S. citizens in Nepal including one victim who filed a writ petition in the Supreme Court, who fell victim to wire fraud and had their funds concealed in Nepal, but these complaints were ignored by the police for an extended period.
Subsequently, with the formation of a new government in Nepal and Rabi Lamichhane assuming the position of Home Minister, the central bureau of the Nepal Police has investigated the case.
On January 6, 2023, the CIB of the Nepal Police arrested Prithvi Bahadur Shah and six associates, including his brother Bijya Bikram Shah, Chakra Bahadur Khatri, Anup Khadka, Rukmangat Kafle, and Ranga Bahadur Saud.
As part of the multinational investigation involving the United States, Canada, and India, the Federal Bureau of Investigation (FBI) assisted the Central Investigation Bureau of Nepal Police in gathering evidence against Shah, to prove his involvement in an organized crime ring in the U.S., India and Canada.
Following the formal lunched of the CIB investigation in Nepal, the FBI provided various pieces of evidence, victims’ statements, and the necessary documentation to support joint investigations and prosecute the criminal gang in Nepal.
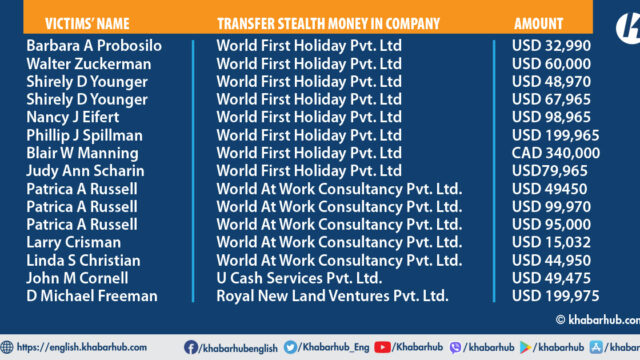
On 13 April 2022, an amount of US$49,180 was received by Citizen Bank (Account no. 0400100000699201) from the same company & later US$19,880 was stolen from the same company. It has been revealed that both amounts were stolen from Paul Kachaturian’s account.
Some crucial documents for the prosecution included a 48-page document on February 1, 2023, a 9-page document on January 22, 2023, a 16-page document on February 1, 2023, and a 43-page document on February 5, 2023, including verifying the authentication of the documents.
As the investigation unfolded, CIB discovered that Shah and his associates had established 24 companies in Nepal.
They deceitfully obtained more than $4.54 million, £22,000 sterling, and CAD 340,000 (equivalent to NPR 639.5 million) by stealthy money of the foreign nationals under the guise of investment in Nepal which was carried out after CIB’s formal written request for help from the U.S. Embassy in Kathmandu.
Sanjay Singh Thapa, the Spokesperson of the Central Bureau of Investigation (CIB), stated that they successfully conducted an investigation involving Prithvi Shah and his network, marking a notable milestone for the Bureau.
He said that after nearly a year of investigation and evidence gathering, the case was initiated following a notification from Nepal Rastra Bank. The FBI and victims filed a case against Shah.
Thapa highlighted the collaborative efforts made in the investigation, particularly with the Nepal Rastra Bank, regarding Prithvi Shah’s alleged involvement in deceiving American citizens through dubious investments in Nepal.
He emphasized that the CIB remained vigilant about the potential for fraud, especially in the context of the rising prominence of digital payments. Furthermore, he stated that if any information from the Nepal Rastra Bank or other sources surfaces, an immediate investigation would be initiated.

According to CIB’s opinion, the District Public Prosecutor’s Office Kathmandu filed four cases – organized crime, fraud, cooperative fraud, and document forgery – against that fraud ring in the Kathmandu District Court. The Kathmandu District Court has sent six individuals including ring leader Shah to judicial custody in March second week, 2023.
Prior to Shah’s arrest in Nepal, the FBI concluded investigations and legal processes in other countries involving the wire fraud gang. As a result, most of the ring members, except one have been imprisoned.
The FBI conducted raids on the residences of the gang members located in the United States. Additionally, Canadian law enforcement agencies, at the FBI’s request, arrested one gang member, while Indian police carried out raids on call centers to gather evidence.
These efforts were part of a coordinated operation aimed at dismantling these wire fraud criminal ring that mostly targeted vulnerable American citizens. FBI special agents have actively participated in missions to apprehend and prosecute gang members, regardless of their location.
Shah’s Foreign Investment Scheme: Tracing the Trail of Stolen U.S. Victim’s Money Transactions
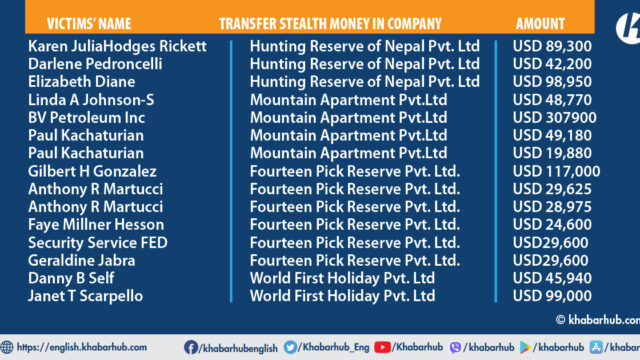
Prithvi Bahadur Shah had deposited the stolen money of $230,450 of Shah’s Hunting Reserve of Nepal Pvt. Ltd., at the Siddhartha Bank Limited (Account no 02420582130).
An amount of $49,800 was deposited to the bank’s account from victim Julia Hodges Rickett on July 19, 2022, and $39,500 on July 20, 2022.
Another victim, Darlene Pedroncelli, reported that her money was stolen on July 22, 2023.
The amount stolen was $42,200, and it was received by the same company as Shah’s.
Darlene informed the FBI special agent about her circumstances with wire fraud, stating, “I received an email claiming to be from the Geek Squad, stating that they were going to withdraw $423.97 from my account. If I wanted to cancel the payment, I was instructed to call 888-216-4073. Since I do use the Geek Squad for computer issues, I called to cancel the payment. I spoke to a person named Sam Watson, who identified himself as Employee #9066geek4049, CPPU6912249.”
She added, “He provided a phone number, 83-915-514-3544. Sam Watson asked me to open my account, and to my surprise, it showed that they had credited $42,200.00 to my account in error.”
According to her, “I was informed that I needed to return the excess amount by wire transfer, otherwise the IRS would get involved and it would become a serious issue. Trusting their story, I went to the bank and wired the money.”
These circumstances highlight the alarming reality of cybercriminal networks targeting vulnerable American citizens who diligently save their hard-earned money, often meant for critical health expenses.
However, over the weekend, she “started feeling uneasy about the situation”, so she visited the bank on July 26, 2022, three days after the wire transfer.
“On August 8, 2022, I received a call from Wells Fargo Bank, informing me that the investigation had been denied and the account of the company in question had been frozen, with no funds available,” she added.
Similarly, on June 19, 2022, an amount of $98,950 was deposited into account number 7501010015455 at Global IME Bank.
This money was also obtained through wire fraud targeting American citizens. Subsequently, the funds were transferred to six local cooperatives based in Kathmandu, Nepal, as part of a money laundering operation.
Four individuals were involved in facilitating this illicit transfer and subsequent laundering process.
Similarly, US$ 425,730 was received by Shah’s Mountain Apartment Pvt. Ltd., and various commercial bank accounts. Likewise, $48,770 was deposited to Global IME Bank account no 3701010007801 from victim Linda A Johnson-S on 7 July 2022.
Upon realizing the gravity of the situation, Martucci promptly visited both Wells Fargo Bank and the Lacey Township Police Department to file reports regarding the incident. Additionally, in an attempt to mitigate potential risks, Martucci wiped his computer clean after the incident occurred.
On 10 May 2022, Prabhu Bank’s account no. 1190152888500019 received US$ 197950, and on 11 May 2022 another US$109,950 was received. This money was derived from U.S. Company BV Petroleum Inc.
On 13 April 2022, an amount of US$49,180 was received by Citizen Bank (Account no. 0400100000699201) from the same company & later US$19,880 was taken from the same company. It has been revealed that both amounts were withdrawn from Paul Kachaturian’s account.
These funds were subsequently transferred through various cooperatives and individuals in an attempt to evade detection and facilitate their escape.
Shah’s third company, Fourteen Pick Reserve Pvt. Ltd., a travel agency, received a total of $259,400 USD, out of which $117,000 USD has been withheld in a bank account following directives from Nepal’s central bank after an urgent request received from the U.S. side.
These funds were identified as part of the wire fraud scheme targeting U.S. citizens and private companies.
Merry Gracia, reachable at +17203451450, and Noelia Gracia (+13314524037) were the individuals who sent the money to those accounts via remittance. Additionally, during that period of transactions, numerous Nepali residents in the USA were found to be connected with Shah.
On August 23, 2021, the company’s account (number 0170000201301), held at NCC Bank, received a sum of $117,000. It has been determined that this money was withdrawn from Gilbert H. Gonzalez and Norma A. Gonzalez.
These circumstances highlight the alarming reality of cybercriminal networks targeting vulnerable American citizens who diligently save their hard-earned money, often meant for critical health expenses.
These individuals, already grappling with life and death situations, find themselves utterly defenseless as their funds are callously stolen through fraudulent schemes, leaving them empty-handed and in dire straits.

Gilberto H Gonzalez, in a written explanation accompanied by complaints and supporting documents, shared his harrowing experience with the FBI special agent.
He described the tragic circumstances he found himself in, stating, “During a routine check-up for my wife’s stomach issues, she was diagnosed with early-stage Alzheimer’s disease. In anticipation of the forthcoming medical expenses, I diligently saved $120,000 in my checking account, along with a modest savings account of approximately $20,000,” Gilberto said.
“At that time, I was in the process of moving $100,000 of the $120,000 into an investment but had not yet decided on the specific investment avenue. I was determined not to lose the $100,000. Unfortunately, around February 1 of last year, I received a diagnosis of stage 4 cancer and have since been undergoing grueling chemotherapy and radiation treatments, with the radiation treatment concluding just last week. I had completed the chemotherapy prior to that,” Gilberto added.
He further stated, “Currently, I am undergoing Keytruda treatment and receiving injections to strengthen my bones, as my cancer has spread to my skeletal system. Last month, in December, due to the overwhelming responsibilities of caring for my ailing wife, I made the difficult decision to place her in a Memory Care Unit. This was particularly challenging as I am still employed.”
Gilberto further attached all the available paperwork he could find, along with a detailed account of the scam, to support his statements.
On January 27, 2022, the same company’s bank account at Prime Commercial Bank Limited, account number 00106325CA, received $29,625.
Additionally, on January 28, 2022, another amount of $28,975 was deposited into the same account. It has been determined that both of these funds were stolen from U.S. citizen Anthony R. Martucci.
The true account of money stolen from a victim and brought to Nepal as foreign investment from the United States was a result of a wire fraud scam orchestrated by a gang of scammers. In January 2022, Martucci received an email on his Thinkpad laptop from an unidentified person (UP). Martucci cannot remember the specific email address used by the UP.

Martucci’s laptop was equipped with the antivirus program, SUPERAntiSpyware. In the email, the sender stated that an amount of approximately $30 was intended to be withdrawn from Martucci’s bank account, but due to an error, a larger sum of money was inadvertently withdrawn. Martucci speculated that the initial $30 could have been a payment for a computer program.
In reality, Martucci had not reviewed his account transactions prior to the incident and discovered that no money had actually been withdrawn from his bank account.
However, in a subsequent email from the unidentified person (UP), they requested Martucci’s bank account information to facilitate reimbursement. Trusting the request, Martucci provided his bank account details at Wells Fargo Bank.
The money that was falsely presented as foreign investment was actually the result of a wire fraud scam. In reality, Janet T Scarpello provided information to the FBI regarding an incident that occurred in March of 2021. She received an email from someone she believed to be associated with Motton antivirus.
Unfortunately, this led to two unauthorized withdrawals from Martucci’s bank account: $29,625 on 01/27/2022 and $28,975 on 01/28/2022, resulting in a total loss of $58,600.
Upon realizing the gravity of the situation, Martucci promptly visited both Wells Fargo Bank and the Lacey Township Police Department to file reports regarding the incident. Additionally, in an attempt to mitigate potential risks, Martucci wiped his computer clean after the incident occurred.
On February 1, 2022, the same company’s account at Century Commercial Bank Limited, account number 0010003961CA, received $24,600. It has been confirmed that this money was withdrawn from the account of Faye Millner Hesson.
During his formal statement taken by an FBI special agent, she said, “I received an email asking me to pay for a service I had not received. I believe the email was from Geek Squad. The email instructed me to go online to type in an amount, I believe to be $25.00 USD. The amount that appeared on the screen was $25,000.00 USD.”

She added, “I tried to correct the amount but was unable to do so. I then received a message stating someone would call me with further instructions and a phone number was provided. I called the number provided and was told due to a system error, an overpayment was being processed.”
“I was told due to a difference in banking systems, they could not pull the difference in the overpayment electronically, and I would need to wire money to the account number provided. I was instructed by the individual on the telephone to go to the bank and request the wire transfer,” according to her.
She further stated, “The individual on the phone sounded like a male with a foreign accent, possibly middle eastern. I believe I was told by the individual on the phone to say the transfer was for vacation, I recall the individual mentioning something about having to pay taxes if I disclosed to the bank the true purpose of the transfer.”
According to her, she was instructed to call the individual back once the transfer was complete.
“After leaving the bank I returned to my car and called them back. I told them the wire had been sent, and that was the end of the conversation. After the transaction, I began to feel something was not right with the situation. I went home and notified my son Tom. Tom told me to immediately return to the bank and cancel the transaction,” she said.
The bank notified that the funds had already been received and the transaction could not be canceled.
“I took no further action after leaving the bank. As a result of this activity, I experienced stress and anxiety, I was afraid that my identity could now be compromised and this could happen again. My retirement planning and future investment opportunities were affected, as my only income comes from my pension and social security payments,” she said.
On February 9, 2022, an amount of $29,600 was deposited into Shah’s account, which was later identified as money obtained through wire fraud, stolen from Security Service FEDCU and Rafael Dozen.
Additionally, on February 11, 2022, another $29,600 was deposited into the same account, originating from the illicit funds obtained through wire fraud from victim Geraldine Ibrahim.
In a formal statement given to the FBI special agent, Shah explained the events as follows: “On February 8th, 2022, I received an email from the Geek Squad regarding a subscription renewal. The email instructed me to call 1-888-237-5851 for cancellation.”
“I called and spoke to a person named Adam Brown, who claimed to be an employee with employee ID 686 5201. He advised me to call 888-237-5851 and spoke to someone named James, who identified himself as a Geek Squad representative,” he said.
Shah said, “According to James’ request an access to my computer, I granted. He claimed that he wanted to return the money to my bank account. As I logged into my account, he instructed me to enter $300. However, due to an error, I mistakenly entered $30,000 without adding the decimal point. Before I could correct the mistake, he processed the transaction.”
Shah utilized the same transaction methods, promptly transferring the funds to various cooperative and personal accounts.
Another company owned by Shah, World First Holiday Pvt. Ltd, received a total of $881,725 and CAD 340,000 during the course of 2020 and 2021. These funds were sent by Mexican hackers Alfonso Flores, who can be reached at [email protected] and +524773298244 & +524773701785.
On March 17, 2021, the company’s account at Prabhu Bank, account number 1110150987400012, received $45,940, which was identified as stolen money belonging to Danny B. Self. Furthermore, on March 19, 2021, the same account received another $99,000, which was also stolen money, this time belonging to Janet T. Scarpello.
“Approximately two years ago, I contacted a company with the intention of purchasing software for personal use. During the conversation, the individual offered assistance in installing the software. However, they insisted on taking control of my computer to carry out the installation.”

The money that was falsely presented as foreign investment was actually the result of a wire fraud scam. In reality, Janet T Scarpello provided information to the FBI regarding an incident that occurred in March of 2021. She received an email from someone she believed to be associated with Motton antivirus.
In the email, it was mentioned that V2’s Norton service had been renewed for three years at a cost of $249.99, which seemed unusually high considering V2 typically purchased one-year services at a much lower price.
V2 decided to call the telephone number provided in the email to request a refund for the $249.95 charge.
On the call, she spoke with a man named Alex Maxwell who assured her that they could credit the amount back to her account. Maxwell proposed guiding her through the process virtually, using her computer.
Trusting Maxwell, V2 granted him remote access to her computer. He pulled up her bank account information, showing the $249.99 charge. Following his instructions, Maxwell asked V2 to press the “93” keys on her keyboard to initiate the refund.
Unfortunately, when V2 pressed the keys, her computer froze. In an attempt to resolve the issue, she pressed the “9” key multiple times.
Once her computer unfroze, she was shocked to discover that she had unknowingly transferred $99,900 to her own bank account. Realizing the severity of the situation, she promptly ended the call with Maxwell and shut down her computer.
The following day, V2 received calls from Maxwell, who instructed her to visit her bank and wire transfer the amount of $99,900.
To further facilitate the process, Maxwell sent her an email containing the wiring details on March 18, 2021.
On that day, V2 initiated a wire transfer from her Bank of America checking account (Account number 229009890***) to a bank account (1110150987400012) held at Prabhu Bank in Nepal.
Realizing the severity of the situation, V2 promptly reported the incident to both the FBI and Bank of America.
In response, Bank of America took immediate action by opening a new bank account for V2 and assigning a fraud investigator to handle the case.
The assigned fraud investigator provided V2 with a claim number, 19MAR2021-256279, for reference.
During the investigation, V2 mentioned that she recognized the name James Morgan, who had previously emailed her in connection with this incident.
Furthermore, on March 9, 2021, it was discovered that the company’s account at Siddhartha Bank was also involved in this fraudulent scheme.
On March 21, 2021, the company’s account at Himalayan Bank, account number 03909221890019, received a total of $60,000, which was identified as stolen funds belonging to Walter Zuckerman.
According to FBI documents based on the information from him – Walter Zuckerman (Zuckerman) received an email from McAfee advising his account had been charged $1,000. Zuckerman became concerned and called the phone number listed in the email.
Zuckerman spoke to an individual (name unknown) who told him someone was trying to hack his account.
Zuckerman completed two (2) Zelle transfers in the amount of $2,000, and began speaking with an “official” at Citibank, N.A who told Zuckerman his computer had been frozen. The official convinced Zuckerman to wire an additional $60,000 to Nepal to prevent further losses.
Zuckerman realized he made a mistake as soon as the funds were transferred. Zuckerman contacted his son, an attorney, who advised him to file a report with the Nassau County Police Department.
Zuckerman closed his Citibank, N.A. account and moved his retirement funds to a different financial institution.
Zuckerman also got rid of the computer he used during this timeframe. These events had a significant psychological impact on Zuckerman.
Zuckerman experienced deep depression and now regularly deletes emails and ignores phone calls.
Additionally, the company received funds from various victims through its Global IME Bank account C101010000270.
On October 29, 2020, an amount of $48,970, which was identified as stolen money belonging to Shirley D. Younger, was deposited into the Global IME Bank account.
Furthermore, on November 5, 2020, an additional $67,965 belonging to the same victim was deposited into the company’s account as the name of foreign investment in Nepal.
On November 11, 2020, a wire fraud amount of Canadian Dollar (CAD) 340,000 belonging to Blair W. Manning was deposited into the same Kathmandu-based company’s account at Global IME Bank.
On December 20, 2020, the company’s account received a stolen amount of $147,965 belonging to the victim Judy Ann Scharin. Additionally, on December 21, 2020, the same victim’s account was further deposited $79,965 into the company’s account.
World At Work Consultancy Pvt. Ltd., another company owned by Shah, received a total of $244,420, which was identified as stolen money belonging to U.S. citizens.
That money was sent to Nepal by wire fraud. His same Consultancy received Siddhartha Bank Limited account number 50215025904, received funds from the victim Patrica A. Russell in three separate transactions.
On March 3, 2021, an amount of $49,450 was deposited. On March 4, 2021, two deposits were made, one for approximately $99,970 and another for $95,000. Finally, on March 5, 2021, another deposit of $95,000 was made.
Likewise, another company under Shah’s name, U-Cash Services Pvt. Ltd., also received stolen funds amounting to $49,475 like other companies in wire fraud money.
On May 17, 2022, the victim John M Cornell deposited the money into Shah’s company account at Prabhu Bank, account number 1000152556800012.
Similarly, on May 30, 2020, Shah’s Royal New Land Ventures Pvt. Ltd., Account number 04001529213000, received another sum of stolen money, totaling $199,975. That amount was sent by this individual (+919329722151) to Shah, at that time when they were residing in Kenya.
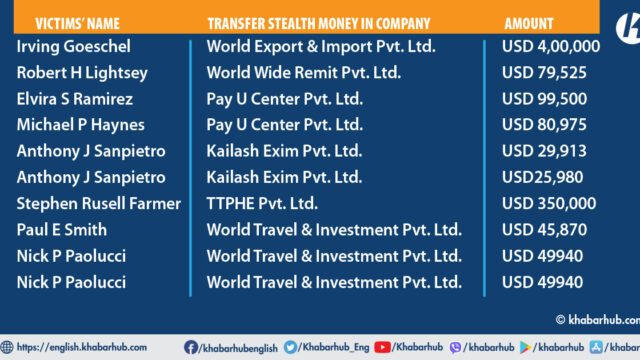
On March 30, 20221, another company affiliated with Shah, World Export and Import Pvt. Ltd., received a sum of $400,000, which was identified as stolen money belonging to Irving Goeschel.
The company deposited the money twice into Mega Bank Account number 0570016759239 on April 24, 2022. The first deposit amounted to $29,913, followed by a second deposit of $25,980.
The funds were transferred by (+919574689216) and deposited into Prabhu Bank account number 1110151248300010.
Another company associated with Shah, World Wide Remit Pvt. Ltd., received stolen funds from a U.S. citizen.
On December 22, 2022, the company’s Global IME account number K801010000356 received $79,525, which was identified as stolen from Robert H. Lightsey and Susan Lightsey.
During the statement to the FBI agent, the victim explained the following:
“Approximately two years ago, I contacted a company with the intention of purchasing software for personal use. During the conversation, the individual offered assistance in installing the software. However, they insisted on taking control of my computer to carry out the installation,” Lightsey said.
Lightsey added, “To facilitate the payment for this service, I was requested to authorize deductions from my savings account at USAA. Unfortunately, once the individual gained access to my USA account, they demonstrated their ability to effortlessly withdraw funds. In order to restore my depleted account, the individual pressured me to wire funds to a company in Nepal.”
He further stated, “Desperate to recover my savings, I reluctantly agreed to proceed with the wire transfer. Subsequently, on or around December 23, 2020, I visited a branch of Trust Bank to initiate a wire transfer. An amount totaling $79,525 was wired to World Wide Remit, which is purportedly associated with the Global IME Bank in Nepal.”
He added, “I later spoke to people at Truist to see if there was any way that I could halt or reverse the transaction, but the sense I got was that, while the Global IME Bank acknowledged the transaction, there was no way I could after the fact force them to return those funds.”
During that period, the Financial Crimes Enforcement Network (FinCEN), a US government agency operating under the Department of the Treasury, took swift action and issued an urgent request to the Financial Intelligence Unit of Nepal Rastra Bank.
The request was to freeze the unlawfully acquired funds and promptly facilitate their return to the United States.
Shah’s other company, Pay-U Center Pvt. Ltd., also received a total of $180,475 from stolen money.
On December 10, 2020, the company’s Global IME Bank Ltd account number 0401010000566 received $99,500, which was identified as stolen money belonging to the victim Elvira S. Ramirez.
“I received a phone call from a person named James Morgan, who claimed to be associated with NEQTEK. Morgan contacted me through the telephone number (786) 352-8684 and offered computer maintenance and security services for a fee,” Ramirez said.
“He insisted that I provide him with access to my computer for this purpose. Feeling intimidated, he emphasized that he would assist me with my Apple security,” Ramirez added.

He continued to add, “Morgan then informed me that there had been an overpayment in my account and assured me that he would refund the unused portion of the virus maintenance fee service.”
“He directed me to access my computer and instructed me to press “Ctrl + Alt.” To my surprise, I witnessed an amount of $100,000 appearing on the screen, which was allegedly the amount I now owed them,” he said.
According to him, Morgan instructed him to click “Ctrl + Alt” again, claiming that his multiple clicks resulted in the $100,000 debt.
“To resolve the situation, he informed me that I would need to perform an overseas wire transfer in order to return the alleged overpayment. I expressed my lack of funds in my Bank of America account and reiterated my desire to return the money I was told I had been overpaid. Fearful of owing money, I complied with Morgan’s instructions,” Ramirez said
According to Ramirez, Morgan directed him to visit the Navy Federal Credit Union branch on Newtown Road in Virginia Beach, Virginia.
“He specifically instructed me not to engage in conversation with anyone at the bank and advised me to inform them that the wire transfer was intended for my brother’s medical expenses. Following his guidance, I completed the wire transfer form in my car outside the bank branch while Morgan provided instructions on how to fill it out,” he stated.
“On December 9, 2020, I initiated a wire transfer of $99,500 from my Navy Federal Credit Union account, which has the account number 0760854703. Initially, I was informed that I owed $70,000, but later I was told that an additional $30,000 was owed, totaling $100,000 in alleged overpayments,” according to Ramirez.
“This amount encompassed all the money I had, including proceeds from the sale of my rental property. I want to clarify that I did not authorize any cash advances on my credit cards. However, I later discovered that cash advances had been obtained without my consent. It is my belief that Morgan, having gained access to my bank accounts through my computer, orchestrated these unauthorized cash advances as part of the scam,” he stated.
Additionally, on January 28, 2021, the same company’s Sunrise Bank Overdraft Loan account number 1290781574701001 received $80,975, which was stolen from Michael P. Haynes of South Carolina.
Moreover, on December 22, 2020, stolen funds from Katherine L. Green were deposited twice into the account. The first deposit amounted to $29,800, followed by a second deposit of $35,900. She was duped by a wire fraud gang four times, according to an FBI investigation report obtained by Khabarhub.
The funds were sent by individuals following numbers (+919818548184), (+919923192813), (+919999748672), (+919973986920). According to their communication with Prithvi Bahadur Shah, two of them claimed to live in Singapore, while one claimed to live in Canada.
Another company associated with Shah, Kailash Exim Pvt. Ltd., also received stolen funds totaling $55,893 from U.S. citizen Anthony J. Sanpietro.
The company deposited the money twice into Mega Bank Account number 0570016759239 on April 24, 2022. The first deposit amounted to $29,913, followed by a second deposit of $25,980.
The funds were sent to Shah’s company account by facilitated by (+919811577218), a member of the Hacking Network gang.
On May 20, 2021, a U.S. citizen named Stephen Russell Farmer’s $350,000 was stolen, which was then deposited into Shah’s company account at Times Today Peace Holiday Environment Pvt. Ltd., held at Kumari Bank with account number 0130113302600001.
Upon discovering the theft, Farmer took immediate action by contacting the appropriate authorities in the USA to report the incident.
Additionally, Farmer sent an email to Kumari Bank, urgently requesting them to halt the ongoing transaction. Realizing the urgency of the situation, Farmer persisted in sending emails to senior staff members of both banks, urging them to take immediate steps to stop the process.
He stated in the emails that the money in question belonged to him and requested that it be transferred back as it was his personal funds.
He filed a case with Nepal’s Supreme Court in an effort to initiate legal proceedings and fight for the return of his money. Despite his efforts, he has encountered challenges and has been unable to recover his funds thus far.
Farmer said to FBI special agent during the formal statement collection in the case: “When I discovered that my money had been unknowingly transferred through unauthorized access to my computer by a wire fraud gang, I felt a sinking feeling in my heart. I knew I had fallen victim to a scam.”

According to him, the bank staff confirmed that my account balance was only $13,000 and some change, while my balance before any transactions on that day was $363,533.22.
“This confirmed that the money had already been sent out. I pleaded with the bank staff for immediate assistance, and they assured me that they would alert the BB&T Criminal Investigation Team right away,” Farmer added.
“After ending the call with Ashley, I began researching Kumari Bank Limited. Through a series of emails and text messages, I was able to locate a phone number for Anil Dhakal, the Branch Manager at Kumari Bank in Aalapot. I dialed the number and attempted to communicate with Dhakal, but the connection was poor, and there was a slight language barrier. Eventually, I hung up,” he maintained.
“Shortly after, I received a text message from Mr. Dhakal expressing his difficulty in understanding me. He provided me with his email address ([email protected]), and I promptly sent him four emails pleading for his assistance in stopping the wire transfer. Mr. Dhakal forwarded my request to the Swift department for further processing and assured me that they would halt the transfer of funds (dated 5/21/2021 at 3:28 am). In my efforts, I also sent emails and texts to any accounts associated with Kumari Bank that I could find,” he lamented.
“On 5/21/2021 at 1:46 am, I received an email from Santosh Kumar Mahato, the Head of Central Remittance Department, requesting more information about the transfer and instructing me to contact Kumari Bank. I promptly provided Mr. Mahato with specific details regarding the fraudulent transaction. In response, on 5/21/2021 at 3:29am, Mr. Santosh Mahato informed me that he had put the funds on hold for the time being. However, in order to return the funds back to my account, further authentication was required,” according to him.
The funds were sent to facilities by wire fraud gang members (+971528840403), (+919574689216), and (+919205211501).
Another company associated with Shah, World Travel and Investment Pvt. Ltd., has received a total of $553,895 in wire fraud funds. The funds were deposited into the company’s Global IME Bank account number 11801010000271 and were received in seven separate transactions throughout 2020.
On September 4, 2020, a sum of $45,870, identified as stolen money from Paul E. Smith and Jeanette Dianne, was also deposited into the account.
On October 16, 2020, a sum of $49,940, identified as stolen money belonging to Nick P. Paolucci, was deposited into the account. Similarly, on November 20, 2020, another $49,940, also stolen from Nick P. Paolucci, was deposited into the same account.
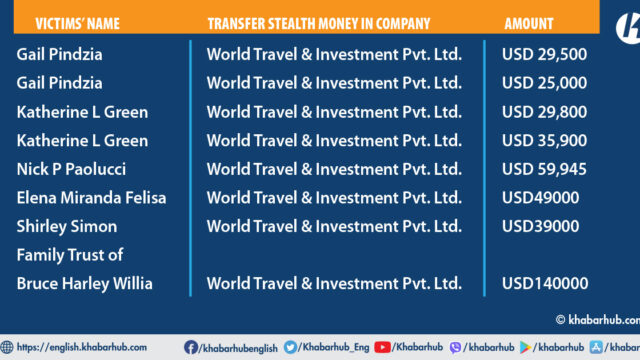
Furthermore, on December 18, 2020, an amount of $29,500, identified as stolen money from victim Gail Pindzia, was deposited into the account. Additionally, on December 20, 2020, another sum of $25,000, also stolen from Gail Pindzia, was deposited into the same account.
FBI report said on her case about what actually happened in that wire fraud: “On or around December 17, 2020, Gail Pindzia (“Pindzia”) received an email from a company called, “Dental Probiotics,” using email address [email protected].
The email contained a detailed invoice for $258.74, regarding a six-month subscription for dental products.
Pindzia called the “customer care expert” telephone number provided on the invoice (877) 846- 9747.
Pindzia initially spoke with an individual who identified himself as “Robbie.” Robbie indicated that Pindzia had $4155.98 in her checking account and the Dental Probiotics would bill an additional $258.74, as described in the invoice.
Pindzia was contacted by another employee of Dental Probiotic who identified himself as, “Mike Williams” using the telephone number (407) 418-8187 and email address [email protected]. In order to cancel the order and receive a refund, Williams instructed Pindzia to open her bank accounts so they can deposit the refund into her account. Williams used “remote access” to gain control of Pindzia’s computer.
FBI report further said “Williams said there was an error where they accidentally placed a large amount of money into Pindzia’s account. Williams told Pindzia that if she did not return the money, Williams would lose his job.”
Despite ongoing wire fraud investigations, Shah’s associates continue to engage in illicit transactions. One of Shah’s associates, Anup Khadka, made two transactions totaling $14,400 in the last week of July 2022 from his personal account at Siddhartha Bank.
As a result, Pindzia was instructed to send two wire payments to World Travels & Investments P.LTD. Pindzia was instructed to keep “an open line of communication.” Pindzia did not hang up the telephone number while she went to the bank to conduct the wire transfers.
Notably, specific evidence found on Shah’s mobile devices included banking details such as account names, numbers, addresses, and routing numbers associated with illicit transactions conducted in the United States. These findings served as crucial evidence linking Shah to the fraudulent activities orchestrated by the gang.
On or around December 17, 2020, Pindzia was instructed to send a wire transfer to “World Travels & Investments P.Ltd.,” bank’s name Global Time Bank, Account Number Cl0101000271, Swift Code GLBBNPKA, account address Chabihal 07 Kathmandu, Nepal, 44600. Pindzia realized she was scammed and filed a Federal Bureau of Investigation (FBI) Internet Crimes Complaint Center (IC3) report.
Moreover, on December 22, 2020, stolen funds from Katherine L. Green were deposited twice into the account. The first deposit amounted to $29,800, followed by a second deposit of $35,900. She was duped by a wire fraud gang four times, according to an FBI investigation report exclusively obtained by Khabarhub.
On September 17, 2020, a sum of $40,000, identified as stolen money from the Family Trust of Bruce Harley Williams, was deposited into the Shah company’s account at NMB Bank.
Similarly, on February 19, 2021, the company’s account at Siddhartha Bank, Account number 00115200706, received $59,945, which was identified as stolen money from Nick P. Paolucci.
On March 19, 2021, the company’s account at Kumari Bank, Account number 0190012891800001, received stolen funds totaling $49,000, which belonged to Elena Miranda Felisa.
Furthermore, on March 24, 2021, the company’s account at NCC Bank, Account number 0030003449501, received a deposit of $39,000, identified as stolen from Shirley Simon.
It appears that multiple individuals, including from Canada (+13316430108), the United States (+13162510057), and India (+919211292455, +918826432478), were involved in transferring the stolen funds.
These individuals’ accounts were used to receive the wire fraud money orchestrated by U.S. based wire fraud gang directly connected with Prithvi Bahadur Shah in Nepal. The involvement of multiple persons and their accounts suggests a complex network associated with Shah’s fraudulent activities.
Likewise, the banking transactions indicate that Shah has been involved in such scams for at least six years, indicating a long-standing pattern of fraudulent behavior.
On December 22, 2022, Shah’s personal account at NIC Asia Bank, account number 378792244252400, received a sum of $24,965, which has been confirmed to be stolen from American citizen KAREN A. EDWARD J PAPP JR.
Furthermore, on April 6, 2017, Shah’s personal account at Nabil Bank Ltd, account number 1701017500540, received GBP 2,860, which was proven to be stolen from Heather Grace Murray and Mr. Ronald.
Additionally, on April 13, 2017, the same Nabil Bank account received another deposit of GBP 2,965, which was identified as stolen from Professor Michael David Wheeler.
In March 2017, Prithvi Bahadur Shah received a deposit of GBP 700 in the same account, which was confirmed to be stolen from Andrew Rockingham.
Furthermore, on December 17, 2017, Shah’s account at Sunrise Bank Ltd, account number 0600405816214001, received a sum of $13,975, which was identified as stolen money from Donna L Anderson.
Similarly, he received a deposit of $49,970 on his Sunrise Bank Ltd account, which was confirmed to be stolen from Campbell Communications Inc.
On March 26, 2017, another person associated with Shah received a deposit of GBP 9,175 in their account at Global IME Bank, account number 3702010000299.
The deposited amount was confirmed to be stolen from Andrew Rockingham.
Similarly, on November 2020, Shah’s same IME account received a deposit of $51,965, which was identified as stolen from Nancy J. Eufert.
Furthermore, on December 16, 2020, the IME account received a deposit of $31,970, which was confirmed to be stolen from the Danielson Family Trust.
Similarly, Shah’s brother, Bijay Bikram Shah, also received $39,130 in stolen money from U.S. citizens. On December 11, 2020, Bijay Bikram Shah’s account at Global IME Bank, account number 0407010007265, received a deposit of $27,970, which was confirmed to be stolen from wire fraud victim DEBORAHA HERRING.
Despite ongoing wire fraud investigations, Shah’s associates continue to engage in illicit transactions. One of Shah’s associates, Anup Khadka, made two transactions totaling $14,400 in the last week of July 2022 from his personal account at Siddhartha Bank.
Likewise, on December 13, 2020, another deposit of $39,482 was made into Bijay Bikram Shah’s account, and it was identified as stolen money from JOHN D BENCKERT JR.
Shah utilized another person named Sagar Ale, whose personal account at Prabhu Bank, account number 137019126150001, received $103,405 in stolen money.
On July 8, 2022, Sagar Ale’s account received a deposit of $44,430, which was confirmed to be stolen from Home Expressions LLC.
“A mutual legal agreement is crucial to dealing with such complexities. Such an agreement offers significant facilitation for conducting joint law enforcement cooperation and investigations between the two countries,” he stated.”
Similarly, on May 10, 2022, the same account received another deposit of $58,975, which was also identified as stolen from the private company Home Expressions LLC.
Despite ongoing wire fraud investigations, Shah’s associates continue to engage in illicit transactions. One of Shah’s associates, Anup Khadka, made two transactions totaling $14,400 in the last week of July 2022 from his personal account at Siddhartha Bank.
These funds were confirmed to be stolen from Betty L SCRANAGE, and the hackers transferred the money to Nepal.
Another associate linked to Shah’s gang, Ranga Bahadur Saud, received a deposit of $13,365 on May 23, 2022, in his Prabhu Bank account (account number 13501300756135000001).
The funds were stolen from Jimmy R Teague’s account.
In addition, Binita Tamang’s Global IME Bank account (account number 00407010007889) received $69,565 on December 15, 2020, which was identified as stolen from the Danielson Family Trust account.
Similarly, on December 22, 2020, Lagam Remi’s account at Global IME Bank (account number 19707010004187) received $95,532, which was stolen from John Cscalia. These fraudulent transactions were facilitated by individuals through Viber and whats app (+13162510057), (+919211292455, +918826432478), (+13316430108).
Meanwhile, Hemanta Malla adds, “While it is the responsibility of the police force to carry out investigations in criminal cases, he pointed out that the involvement of influential politicians, the Cabinet, and the political system in protecting the accused complicates the investigation process.”
“This complexity and doubt surrounding the investigation obstruct the prosecution of the accused and further undermine the overall credibility of the investigation,” he added.
Malla emphasized the need for close coordination between government agencies to effectively investigate and prosecute Prithvi Shah’s involvement in international wire fraud.
“Investigations of this nature require the collection of evidence from multiple government agencies, both within and outside the country. Therefore, close coordination becomes an absolute necessity due to the differing mandates and responsibilities of these agencies.”
Malla added, “In the realm of organized crime, low-level criminal gang operators receive necessary protection from the top echelons. The lower-level criminals heavily rely on and are under the control of the higher-ranking members.”

According to him, the individuals at the higher levels who offer protection receive a significant portion of the illicit proceeds in order to avoid trouble and evade law enforcement agencies.
“It is crucial to conduct a comprehensive investigation into the higher-ranking individuals who provide such protection, delving into their motivations, the benefits they receive, their connections to the accused, and ultimately resolving all pertinent questions.”
He added, “Failure to thoroughly investigate the upper-level protectors will leave doubts about the integrity of the investigation, fostering lingering suspicions and rendering it incomplete.”
Malla further added, “Investigating organized and transnational crimes poses certain challenges due to the different laws and practices in different countries. Each country has a different approach and practice for dealing with such crimes, resulting in different legal frameworks for specific types of crimes.”
Notably, specific evidence found on Shah’s mobile devices included banking details such as account names, numbers, addresses, and routing numbers associated with illicit transactions conducted in the United States. These findings served as crucial evidence linking Shah to the fraudulent activities orchestrated by the gang.
According to him, to address these investigation challenges, mutual legal treaties are necessary for effective cooperation. For example, certain acts that are considered crimes in Nepal may not be considered crimes in the United States, and vice versa. Such disparities can complicate investigations and hinder cooperation efforts.
Therefore, establishing legal agreements that can adapt to the evolving nature of crimes is essential.
“Let me give an example: The case of Pawan Karki, a bank fraudster who is wanted by Nepalese law but remains at large in America, where his actions are not considered criminal under US law,” he said.
According to him, in cases of organized crime, offenses often occur across multiple jurisdictions, requiring investigations from various angles. Cooperation among law enforcement agencies from multiple countries becomes imperative in such transnational investigations.
“A mutual legal agreement is crucial to dealing with such complexities. Such an agreement offers significant facilitation for conducting joint law enforcement cooperation and investigations between the two countries,” he stated.”
During the investigation into Prithvi Bahadur Shah’s activities, several technical aspects played a crucial role in confirming his connection with members of the International Wire Fraud Ring.
Abhaya Raj Joshi, the Executive Director of Nepal Centre for Security Governance (NCSG), a think tank based in Kathmandu, emphasized the significance of the Prithvi Bahadur Shah case.
He raised important questions: “What lessons can Nepal derive from this experience? How can law enforcement agencies, especially those engaged in international police cooperation, strengthen their effectiveness and enhance their procedures?”

He further emphasized, “The case of Prithvi Bahadur Shah underscores the crucial role of strong international police cooperation and underscores the necessity for law enforcement agencies to establish robust procedures.”
According to Joshi, Nepal can derive valuable lessons from this experience. These lessons include the significance of prompt and accurate communication among law enforcement agencies, the necessity of utilizing advanced technology for proper documentation and record-keeping, and the importance of adhering to established procedures and protocols.
“To enhance their effectiveness and improve their procedures, law enforcement agencies, especially those engaged in international police cooperation, can take several proactive measures,” he proposed.
He recommended prioritizing investment in advanced training and capacity building for officers involved in international cooperation, formulating clear and consistent procedures for handling international cases, and establishing robust communication channels with their international counterparts.
“Furthermore, law enforcement agencies can harness the power of technology and data analytics to enhance their effectiveness,” added Joshi.
He emphasized the utilization of advanced data analytics tools to identify patterns and trends in criminal activity. Additionally, leveraging technology to facilitate seamless communication and collaboration between law enforcement agencies across borders is essential.
He went on to express, “In conclusion, the Prithvi Bahadur Shah case serves as a powerful reminder of the significance of effective international police cooperation and highlights the continuous need for law enforcement agencies to consistently evaluate and enhance their procedures in order to maximize their effectiveness.”
How technical investigation ensured Prithvi Bahadur Shah’s involvement?
During the investigation into Prithvi Bahadur Shah’s activities, several technical aspects played a crucial role in confirming his connection with members of the International Wire Fraud Ring.
Shah used multiple phone numbers, with his primary communication channels being Viber and WhatsApp, through which he connected with the international Wire Fraud Ring.
The phone numbers he used to establish these connections are as follows: Viber and WhatsApp: +9779851050427; +9779851239445; +97798512224427; +9779802050427; +9779803946920; and +9779801267901.
In addition to his phone communications, Shah also employed various email addresses to communicate with the gang members. The email addresses he used include: [email protected]; [email protected]; [email protected]; [email protected]; [email protected]; [email protected]; [email protected]
[email protected]; and [email protected]
The gang sent a multitude of fraudulent documents, including counterfeit U.S. passports, driver’s licenses, and other necessary paperwork to facilitate the completion of all legal procedures required for withdrawing money from Nepali banks. These documents were carefully crafted to deceive authorities and gain access to the funds.
Additionally, another compelling piece of evidence discovered on the mobile device was a video file named VID-20221020-WA0009. This MP4 video depicted a cash package, further strengthening the case.
The connection between Prithvi Shah’s WhatsApp number and various foreign numbers during, before and after the banking transactions were: +918800309866, +919810814827, +9143603920, +917042552122, +919899393697, +91 9329722151, +9195746 89216, +919654493626, +918860852750, +919811577218, +9198-18548184, +919923192813, +919999748672, +919973986920, +919211292455, +918826432478, +971528840403, +9195746 89216, +91 92052 11501, +13316430108 (Canada), +13162510057, +61416086197, +1347 244-1682, +17038443276, +13472441682, +17038443276, +971528840403, +971528840403, +17203451450, +13314524037, +971507506471, +971507862576, and +971557743777.
The evidence obtained from Shah’s mobile devices solidified his involvement in the international wire fraud scheme ring.
The data retrieved from his mobile devices provided substantial proof of knowing and an unknowing connection with the fraud ring members with direct financial transactions.
Communication showed that ring members conspired with each other with the intent to devise a scheme to defraud individuals by means of false pretenses.
The technical investigation yielded valuable evidence regarding Shah’s involvement in an international wire fraud ring.
It uncovered crucial communication channels and banking transactions that provided compelling proof of his connection to the ring.
The examination of Shah’s mobile and other devices revealed critical content, such as photographs of Swift codes and other pertinent information shared by members of the wire fraud gang.
Notably, specific evidence found on Shah’s mobile devices included banking details such as account names, numbers, addresses, and routing numbers associated with illicit transactions conducted in the United States. These findings served as crucial evidence linking Shah to the fraudulent activities orchestrated by the gang.
His Samsung SM-G998BDS Galaxy S21 Ultra 5G mobile device contains evidence, including partially captured photos, suggesting the transmission of substantial sums of money to gang members based in India.
Additionally, another compelling piece of evidence discovered on the mobile device was a video file named VID-20221020-WA0009. This MP4 video depicted a cash package, further strengthening the case.
Other pieces of evidence included: Account Information: Account Name: Radient Health LLC; Account Number: 791868182
Address: JP Morgan Chase, New York, NY 10017, Swift Code: CHASUS33; Bank Routing Number: 021000021.
Another Account Information found in the device was: Account Name: Asmit Wadhwa; Account Number: 765870289; Address: 383 Madison Ave, New York, NY 10017; Zelle Number: +14697730429; Routing Number: 111000025; Account Number: 488052662364; Bank: Chase Bank; Transaction Details: $4,400 deposited, $10,000 cash withdrawal.
These pieces of evidence are directly linked to the misappropriation of funds from the victims.
The technical investigation also revealed the involvement of individuals with American-Nepali backgrounds in financial transactions with Shah, indicating a connection to financial transfers taking place in Texas.
The technical investigation yielded valuable evidence regarding Shah’s involvement in an international wire fraud network. It uncovered crucial communication channels and banking transactions that provided compelling proof of his connection to the network.
During the technical investigation, Shah was found to have communicated with the Former Nepali individuals’ and received money but their involvement and their motives are yet to be verified. Some of these individuals include Maya Gurung (+17203451450), Rahul Kumar Thapa (+13459290636), Om Bahadur Taha (+1345925-1187), Rajendra Shrestha (+1345321-0289), Sailendra Hem Cayman (+13453214881), Indra Kumar Thapa (+1 345925-5794), and Min Bk (+13459165298).
Their money was sent by two individuals: +17203451450 (Likely to be a fake name Merry Gracia) and +13314524037 (Likely to be a fake name Noelia Gracia) sent the money in Shah’s company name Fourteen Pick Reserve Pvt. Ltd.
During the investigation, law enforcement agencies effectively traced the shipment of his parcels. They employed tracking numbers to monitor the packages, meticulously documented delivery attempts, and successfully obtained recipient addresses throughout the process.
Some of them were shipped to Fort Worth, Texas 76131-1771 Residential US, and another at ID 1z884F34449230622 to Forth Worth, Texas, US, Tracking No- 1Z6Y0Y780187624625 Forth Worth, Forth Worth Texas 76137-6904, Tracing number: 1Z945X241554456086, Shipment 09/15/2022.
He went on to express, “In conclusion, the Prithvi Bahadur Shah case serves as a powerful reminder of the significance of effective international police cooperation and highlights the continuous need for law enforcement agencies to consistently evaluate and enhance their procedures in order to maximize their effectiveness.”
It was delivered on 09/16/2022, at 7:26 am. (Delivered to: REGISTERS TOWN.MD US, Tracing No # (MTCN) 143-536-8285; Shipment No: 1Z5379W71578716614: Texas US, JERRY MARK STE 149 5621 BASSWOOD BLVD FORT WORTH TX 76137-6984, Tracking no: 1Z09F25E1555968545 to FORT WORTH, TX US.
The technical investigation yielded valuable evidence regarding Shah’s involvement in an international wire fraud network. It uncovered crucial communication channels and banking transactions that provided compelling proof of his connection to the network.